URL Manipulation and What to Do About It

Most people know what a URL is. It’s the address of a website, typically starting with http:// or https://, and it is essentially the location of a web page or application that can be accessed through a web browser or application. Nowadays, URLs are being manipulated by actors for both positive and negative means. Let’s […]
Cybersecurity: An Origin Story

The way a business handles network security is directly related to what problems will arise from their use of information systems. Cybersecurity has become a major part of all businesses, of all geographic locations, and all sizes. Because the better your cybersecurity is, the less problems your business will have to overcome, cybersecurity has grown […]
Essential Network Security Best Practices

Too frequently, we hear stories about cyberattacks, software vulnerabilities turned tragic, and other pretty terrible situations for businesses. In an effort to help fight this, we’ve put together a list of handy tips for you so that you can be prepared to ward off threats. Leverage Authentication Measures One of the first steps to securing […]
Biggest Data Breaches Since May

Has your business’ network been breached? If not, you will need to continue to prioritize network security to keep hackers at bay. With 446 million records compromised in 2018 alone, businesses need to understand what threats they are currently under. Let’s take a look at some of the biggest data breaches that have happened since […]
How You Should Judge Potential Password Management Programs

Passwords are hard to remember – there’s no denying that. However, there is also no denying how important it is to use different ones for each account, all sufficiently complex, and all the rest. The point is, a lot of people use bad password practices because (to be frank) good password practices are too intimidating. […]
Think Before You Click: Spotting a Phishing Attempt

We’ve all caught the obvious spam email, like the message that is clearly bogus, or the offer that is definitely too good to be true. We’re going to confidently assume none of our readers are getting tricked by Nigerian Princes or getting roped into order virility drugs from an unsolicited email. The real threat comes […]
Even Amazon Can Be Hacked

In 2018, Amazon was struck by a considerable attack, with hackers taking funds from approximately 100 seller accounts, according to a Bloomberg report. Between May and October 2018, Amazon sellers were struck approximately 100 times, draining funds from the seller control platform to augment their own funds. According to the investigation, the first fraudulent transaction […]
Windows 7 and Windows Server 2008 R2 is Finally Losing Support

Microsoft Windows has been a staple of modern computing, with each title in the series offering more innovative features. When it becomes time to retire one of their OSs, it can be troublesome for businesses. This coming January, two of the most utilized versions of the Windows OS–Windows 7 and Windows Server 2008 R2 will […]
How Much Risk Can the IoT Cause?
The Internet of Things is rapidly growing in popularity, which makes it all the more likely that some IoT devices will make their way into your office. Also growing: the reputation that these devices have as vulnerabilities to your organizational security. In an increasingly connected world, it is important to remember how the IoT could […]
The Time Has Come for SQL Server 2008 and 2008 R2

Software solutions don’t last forever. While patches and security updates can stave off the inevitable for quite some time, it’s impossible to maintain a specific solution forever. Support is eventually cut off, and businesses are left exposed if they haven’t taken the time to prepare. In the case of Microsoft SQL Server 2008 and 2008 […]
Even Small Businesses are Targets for Hackers

Do you ever think of your business as too small of a target to matter to hackers? Some organizations actually do believe this, and that notion is effectively a trap. The thing that all businesses need to keep in mind is that all organizations, regardless of which industry they fall into, as all companies have […]
Staff Education Goes a Long Way in Preventing Security Issues

In a perfect world, keeping your antivirus updated and having a good firewall in place would be enough to protect your business from cybersecurity threats. Unfortunately, most attacks still come in through email, and can slip by your users. Even the most complex cybersecurity platforms used by massive corporations and governments can be foiled by […]
Is Blockchain a Shield for Cybercrime?

Blockchain technology is all the rage these days. Business owners are going to start hearing this buzzword as a bullet point in software solutions. Developers from all over the world are trying to harness the power of encrypted, distributed data, mainly due to the reputation that blockchain has regarding the “unhackable” permanence of the data […]
Taking an Exploratory Stab at Spear Phishing
Chances are, you’ve heard of “phishing” – a cybercriminal’s scam that steals data, access credentials, and other sensitive information by fooling a user into thinking they are providing this information to someone who is supposed to have access to it. However, there are a few different kinds of phishing, based on how it is carried […]
Tip of the Week: Your Phone Can Work as Your Security Key
If you’re like most people nowadays, your mobile phone is currently well within your reach (and that’s assuming you aren’t reading this blog on it). The fact that most people keep their phone on them at all times has greatly contributed to these devices becoming a part of any given work-related process. One major way […]
United States Citizens Demand Data Privacy… How Will It Impact Your Business?

With over 90 percent of people in the United States feeling as though their data is out of their hands, it should come as little surprise that many are looking towards the European Union’s General Data Protection Regulation as inspiration. However, how close is the United States to passing this kind of legislation… and how […]
Colleges Have a Lot of Data to Protect

Colleges and universities are part-time homes to more than 16 million people, and employ over 1.5 million more. Most of them utilize the networks set up by the college’s bevy of IT administrators. If you consider that most people have difficulty keeping viruses and other malware off of their personal computers, opening up networks that […]
Getting to Know About Phishing Attacks Can Keep Your Business Safe

There’s a big reason why phishing is a primary threat to businesses, and it’s because this method gives hackers a relatively risk-free way of gaining access to a network or other resources. Even being aware of the issue is often not enough to prevent it, as hackers are known to get quite aggressive and crafty […]
Biometric Authentication Becomes More Commonplace

Biometrics are a common sight in futuristic or science-fiction settings, but they are increasingly entering the real world in practical ways. In fact, similar technologies are being implemented every day for businesses all over the world. Let’s take a look at some of them, as well as what benefits they provide these organizations. What Are […]
Microsoft Launches Office 365 Advanced Threat Protection
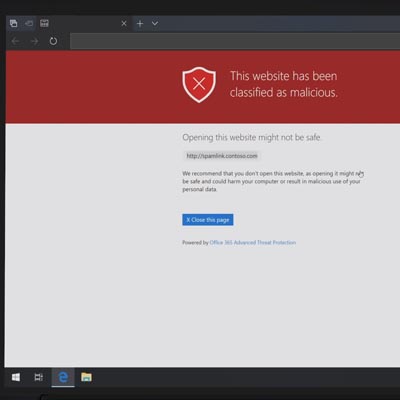
Microsoft has been at the forefront of security through their numerous operating systems for decades. As the security of computing systems and communication gets more important, and with threats to that security growing exponentially, the world’s leading software company has made it a point to introduce a new security platform to help people in many […]
