Getting a Better Sense of Customer Relationship Management

I’m sure I don’t need to tell you how important it is to have a handle on your clients’ needs. After all, how else are you supposed to offer them the level of service that they need to remain satisfied enough to stay subscribed to what you offer? This endeavor is exactly why a customer […]
Tip of the Week: 5 Tricks to Using Windows

There’s a lot more to the Windows operating system than first meets the eye, especially where handy shortcuts are concerned. Today, we’ll cover five of the shortcuts baked into Windows that may be beneficial to your productivity. Rename File Every so often, you will discover that the name of a document isn’t entirely accurate anymore. […]
The Most Devastating Hacks of 2018… So Far

Network security is a crucial consideration for every contemporary business owner, as there are just too many threats that originate from an Internet connection to be overlooked. One only has to look at what businesses of all sizes have dealt with, even within this calendar year, to gain an appreciation for how crucial it is […]
How Much Have Smartphone Cameras Made a Difference?

When it comes to selecting a smartphone, most consumers look to the camera as a major deciding point – after all, many popular applications geared toward the everyday user heavily lean on the use of a camera. This utility and, in some ways, reliance have only encouraged rapid advancement to phone-based camera technology since its […]
Know Your Tech: Proxy Server
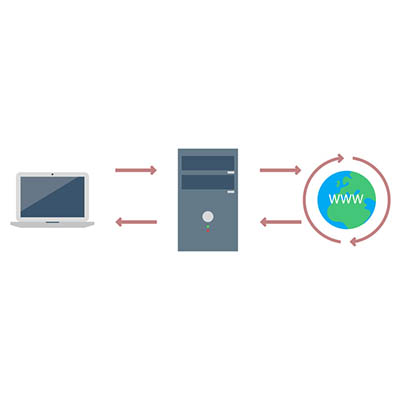
Your server room may be somewhat intimidating to consider. Wires everywhere, mechanical boxes that just sit there, lights blinking intermittently, and the distinct feeling that you probably shouldn’t touch anything – not even a proxy server, whatever that is. However, to help you get to know your tech, the proxy server is exactly what we […]
Our 2018 Business Technology Overview

Businesses have a lot to think about, especially regarding best practices and upcoming trends in technology. Has your business been doing all it can to keep up? We’ve outlined some of the best IT innovations that we expect to see in 2018 as time goes on. Security Worries It should be clear that in today’s […]
Budgeting for IT Can Benefit Your Business’ Bottom Line

Your business depends on a budget to come out in the black at the end of the fiscal year, and the way you invest that budget will have a considerable impact. As you create this budget, your IT needs to be one of your top considerations – after all, it is what effectively powers the […]
Tip of the Week: Avoiding Scams

Uh oh. One of your employees sat down at their workstation and was presented with a pop-up telling them that Microsoft has detected a fatal issue with their workstation, and if they don’t let someone remote in to fix it, all of their data will be lost. This could be a serious problem… especially if […]
What Virtual Assistant Is Right for You?

Virtual assistants are some of the most common technologies out there, which is kind of a strange thing to say. With mobile devices taking over the personal and professional lives of users, we suppose it’s natural that virtual assistants have flourished in today’s workplace. What are these assistants, and what are they capable of? Virtual […]
Hackers Target Major Sporting Events

There are literally billions of sports fans in the world, and the popularity of these events brings in big money; and big money typically attracts hackers. Using all types of methods, there has been a history of hacking in almost every sport. Today, we take a look at some of the most famous hacks that […]
Know Your Tech: A/B Testing

A key component to effectively attracting your audience is to better understand their preferences. Even the most seemingly insignificant change, like changing the color of the buttons on your website, can have a major impact on how effective your materials are. Fortunately, through a process called A/B testing, observing the impact of these changes is […]
Hackers Plus Artificial Intelligence Equals Big Trouble

Thanks to the advent of artificial intelligence, cybersecurity professionals have to reconsider how they approach these threats. Machine learning is one option, as it can help today’s modern solutions learn how to be more effective against advanced threats. On the other hand, what’s stopping the other side from also taking advantage of artificial intelligence? The […]
Attempts to Make Smart Cities Hit a Snag

At this point, the concept of the Internet of Things is a fairly familiar one, but that familiarity is to the Internet of Things on the micro scale–appliances with capabilities enhanced by an available connection to the Internet. There is another, more macro application to the Internet of Things: as a way to collect data […]
Tip of the Week: Set Your System up with the Apps You like to Use

Sometimes you’ll open up a document and it will open up in a default program on your computer that you never use, or one that you might not even know you have. This can happen with common types of file formats, like PDFs or MP3s, that could be opened by more than one program on […]
UTM is a Strong Solution to Ward Off Hackers

When your employees think about hackers and network security, do they picture some cloaked or hooded figure in a dark room typing away at a keyboard? Do they see a recluse living in their mother’s basement? Popular culture has given many users a false sense of reality regarding hacking attacks and the culture surrounding them, […]
Reduce Setup Costs with IT Consulting

It’s always exciting when the idea of a business becomes real by finding a space to conduct operations. It’s extra exciting when a business has outgrown its space and has to move into a new space. Whatever situation you are encountering, it can be excruciatingly difficult to affordably move into new offices. NuTech Services can […]
Tip of the Week: How to Find Success With Remote Workers

Thanks to mobile devices and remote access, businesses around the world are freeing their employees from the tethers of their desks and allowing them to work remotely. Some companies have employees that work remotely all of the time, which presents the question of how you keep them connected to the workplace, productive with their time, […]
The Major Points of A Secure Email Solution

It’s not out of the ordinary for employees to not know the best practices surrounding email management, but it’s something that any self-respecting employer needs to consider. How are your employees using their email, and are they putting your organization at risk? The best way to address these issues is taking a two-pronged approach involving […]
As Augmented Reality Grows, More Applications Appear
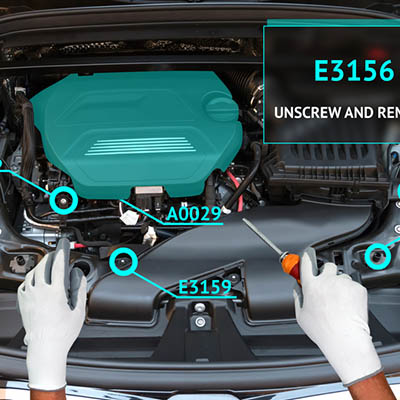
“Augmented reality” is likely one of those terms that you’ve heard before, but that’s more or less your experience with it. However, A.R. has likely been a bigger influence than you may have imagined – especially with the prevalence of smartphones being what it is. Let’s examine augmented reality and how it might be used […]
Know Your Tech: Social Media

You see the term “social media” thrown around all the time, but what does it mean for both individual users and whole businesses? Organizations that understand the importance of social media have a unique advantage over other businesses in the same industry, be it a way to attract more consumers or a way to protect […]
