Tip of the Week: Use Android Doze to Help Save Battery Power

How often have you grumbled as you’ve reached for a charger at 2 in the afternoon as your smartphone clings to its last moments of life? If you’re anything like the typical user, quite often, but Android has attempted to reduce that number with the Android Doze feature. Doze accomplishes this by disabling an application […]
Latest Windows 10 Update Has Kindle Users Feeling Blue… Screen of Death
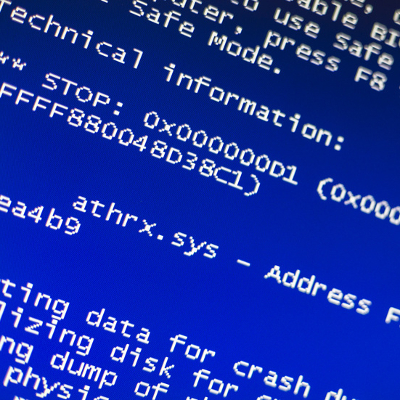
Have you have recently plugged in your Kindle and received a blue screen of death? Many Kindle users have found that Windows 10’s anniversary update is creating an issue in the way that Kindle transfers books and charges via a USB connection. Some users are reporting that connecting a Kindle to a Windows 10 device […]
3 Lessons We’ve Learned for a Successful Cloud Migration

If you’ve recently decided to implement cloud computing for your business, then we commend you. You’ve chosen to use a powerful and dynamic solution for your computing needs. However, choosing to use the cloud and actually implementing the cloud are two entirely different monsters. Now that you have your sights set on the cloud, what […]
Tip of the Week: Why You Should Be Wary of Using Public Wi-Fi

Wireless Internet connections, often referred to by the moniker Wi-Fi, have become a popular offering from public businesses. Even organizations that have no real need for an Internet connection to conduct business, like restaurants and coffee shops, now offer Wi-Fi for their customers. However, public Wi-Fi can be dangerous, especially for the business professional. The […]
Exploits From the NSA are Now on the Black Market

If you panic in the event of a hacking attack, imagine how the National Security Agency (NSA) feels knowing that some of its exploits are for sale on the black market. While there isn’t any proof that the NSA has been breached, there’s evidence to suspect that their exploits are available for purchase on the […]
4 Reasons Why You Should Quit Stressing Out About Stress

Stress is a natural part of the workplace. It’s almost impossible to make it through the workday without getting stressed out about at least one thing or another, especially when you’re a business owner. In these stress-filled circumstances, it’s important to remember that stress isn’t always a bad thing; it has some redeeming factors that […]
Tip of the Week: 3 Expert-Level Search Tips to Help You Find Exactly What You’re Looking For

These days, being able to find the exact information you need online is a valuable skill. However, sometimes a website’s search capabilities aren’t robust enough to be of much use. For this week’s tip, we’ll show you how to combine a website search feature with your browser’s search tool so you can easily find exactly […]
According to Hackers, Windows 10 Security Passes the Test

Windows is perhaps the most common workplace computing tool, and hackers have been trying for decades to uncover holes in its security. In some cases, like with unsupported operating systems, they’ve succeeded. However, Microsoft’s latest addition to their OS family, Windows 10, seems to have exceptionally potent built-in security measures, many of which have the […]
MasterCard Wants Your Selfie, But it’s Not for What You Think it’s For

Payment via mobile devices is still a relatively new concept. With newer smartphones, it’s now easier than ever to pay your bills or send money on a whim. However, this also brings up an important topic; what’s the best way to handle mobile payments, and how can those who accept and process these payments ensure […]
Tip of the Week: How Tracking Your Net Worth Can Benefit Your Long-Term Goals
Tracking your net worth might not be the same as tracking how many much money you have in your account, but it’s a good start. By tracking your net worth, you’ll have a good idea of how your finances fare in the big picture of things. Doing this may even help you worry less so […]
Alert: Microsoft Outlook Users Be Wary of New Ransomware

Ransomware is a particularly nasty strain of malware that continues to pop up in unexpected forms. In the case of a new variant of called Cerber, it targets users of Microsoft Outlook using a zero-day vulnerability via phishing messages. To make matters worse, Cerber can also utilize DDoS attacks, which is a major cause for […]
It Pays to Outsource Your IT

Technology can be fickle at times. When it’s not working properly, it can hold your business back from reaching its maximum potential. Therefore, in order to maximize your bottom line, it becomes common sense to ensure that your technology is in proper working order at all times. The problem lies in the fact that you […]
Tip of the Week: 4 Ways to Make Sure Workplace Instant Messaging Enhances Productivity

Instant messaging has changed the way that individuals communicate with one another, both in their personal lives and in the workplace. Just as email threw a wrench in traditional mail’s plans, instant messaging threatens to jump start a new method of instantaneous communication, one which can be seen as a great benefit, but also an […]
For NATO, Cyberspace is Today’s Frontlines

It’s clear that security professionals have waged war with hackers since the Internet’s inception, but NATO has reaffirmed that cybersecurity is not just a localized problem; it’s a nation-state-wide issue, and one that needs to be addressed. Just like land, air, and sea, cyberspace is now an operational domain, a place that can be considered […]
Why True Autoscaling is Out of Reach for the Average SMB

Shopping for a cloud solution can be difficult. You’ll be sold on plenty of impressive-sounding features that you may not know anything about. One feature that you may have seen floating around is autoscaling, which sounds great on paper, but may not live up to its expectations. The only problem, though, is how you can […]
Tip of the Week: 4 Guidelines When Buying Used Computer Equipment

One way that your business can save money is by purchasing used computer equipment, but only if you do your research and perform a meticulous analysis of where it’s been, and why it’s no longer being used. If you’re serious about purchasing pre-owned computing equipment, consider these four tips. The Hard Drive’s AgeOne of the […]
Couple Jailed for Scamming More Than a Couple Dollars From the IRS

It all goes to show: don’t mess with the IRS. The prison system has two new residents, after Anthony Alika, 42, and his wife Sonia, 27, were sentenced for filing fraudulent tax returns through the often-exploited “Get Transcript” site maintained by the Internal Revenue Service. In addition to their incarceration, the Alikas will each be […]
Study: 95% of All Cyber Attacks are Financially Motivated

Businesses need to take security into account and make it a priority. In fact, security is so important that Verizon has compiled a report of the various types of attacks and data breaches that occurred in the past year. This is Verizon’s Data Breach Investigations Report, or DBIR, and it offers insights into how you […]
Alert: Microsoft’s Latest Patches Address 27 Vulnerabilities

Microsoft recently issued security patches to fix 27 vulnerabilities, many of which are critical in nature. The vulnerabilities are significant and popular titles are affected like Windows, Microsoft Office, Internet Explorer, and the new Edge browser. Microsoft users that ignore these security patches are putting their system at unnecessary risk. If you’ve already applied the […]
Tip of the Week: 4 Easy Ways to Make Working Remotely Work for You

Working remotely is made much easier thanks to today’s modern technology solutions. Many organizations have at least part of their workforce working remotely, but without the proper support, remote work wouldn’t be possible. With the latest technology and a couple of best practices, the remote worker can be just as productive, if not more so, […]
