Your Router Can Host Some Pretty Nasty Malware

Hundreds of millions of people use wireless Internet connections every day, and as a result, hackers are taking that as a challenge. They are now starting to develop malware that targets people through their routers. Recently, security researchers at Kaspersky Lab have discovered the malware named Slingshot. The code is designed to spy on PCs […]
Know Your Tech: Cache

If you hang out around technology professionals for any period of time, chances are that you’ve heard the word “cache” used before. The word, pronounced cash, is usually heard in the phrase, “clear the cache,” but if you don’t know what this phrase means, how can you benefit from it? Since this week’s tech term […]
Why You’ll Want to Consider Hosted VoIP Telephony

Today, communications are an important part of business, and with nearly every organization looking to reduce redundancies, a lot of businesses are starting to take advantage of Voice over Internet Protocol (VoIP) solutions, using the resources they already have in place to avoid paying twice over. With today’s ISPs delivering faster and faster speeds to […]
Where You May be Seeing More AI Soon

The notion of artificial intelligence has played out in fiction, on the silver screen, and on the small screen for decades. Instead of having sentient cyborgs that enslave humanity, people are using A.I for our benefit. Today, we take a look at the A.I. of 2018 and how your business can leverage it for your […]
Tip of the Week: Creating Canned Responses in Gmail

If you’re like most business users, you rely on email quite a bit to stay apprised of what is going on, as do most of the people you are likely in communication with. As such, you most likely understand that, while most emails require some kind of response or confirmation of receipt, not all of […]
Technology Addiction is a Very Real, Very Scary Thing

Technology has become essential to workplace functionality and personal productivity, but while the long hours spent glued to our tech during the workday are a necessity, the time we spend at home with our personal devices is definitely voluntary. However, more and more people – children especially – are finding it harder to let their […]
Is Your Cloud Solution Actually a Money Pit?

The cloud has proven to be an extremely useful tool for the modern business. Not only does it provide anywhere-anytime access to applications, processing, storage, et al; it also delivers those products as a service, allowing you to budget for recurring costs rather than major upfront ones. This provides your organization with functional, supported, and […]
Tech Term: Computer Forensics, Defined

Pop culture gives us an impression of what cyber investigations look like. Official-looking people, in impeccable suits, typing away at terminals and analyzing the data scrolling past them on their heads-up displays. In reality, computer forensics (as they are actually called) are a little less dramatic, and much more serious. For today’s tech term, we’ll […]
Monitoring and Automation Make for a More Secure System

Information technology, in many ways, is a necessary evil. Sure, modern businesses more or less require it to remain competitive, but it also opens up your business to a multitude of threats. Maintaining your security is made much easier with automated monitoring tools. Today, we’ll discuss how to use these tools to protect your business. […]
What Star Wars can Teach About Mentorship

The Star Wars saga has many recurring themes – the struggle between desire and destiny, good and evil, impulse and discipline. However, a theme that particularly stands out throughout the series is the examination of the relationship between student and teacher. This theme is similar to the relationship that an IT provider should strive to […]
Tip of the Week: Working from Google Home

It is no secret that Google can serve a great utility in the office through its many services and applications. However, have you ever considered how the Google Assistant can, well, assist you through devices like your smartphone and the assorted smart speakers that Google has produced? For today’s tip, we’ll review how some of […]
These 3 Industries are Being Fundamentally Changed by Smart Technology

Smart technology has seen explosive growth in recent years, leading to an uptick in startups popping up to capitalize on smart tech and the innovative ways it can be leveraged. With demand for such devices increasing exponentially, it’s little wonder that many industries are diving into this technology. Today, we’ll discuss three of them. Energy […]
What is Nanotechnology, and How Can it Be Used?
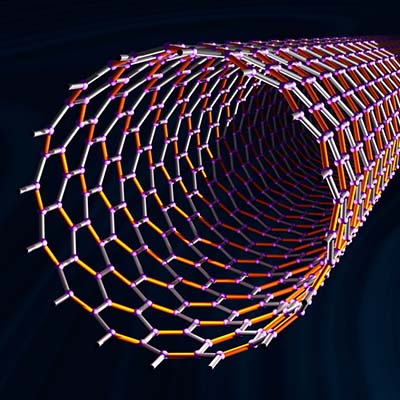
Technology is seemingly being made smaller and smaller. Just think about the size of the computers from the mid ‘90s until now. Sure, you can still buy huge a gaming PC with a four-foot tower with liquid cooling, or one that is a fish tank (complete with fake fish); but, the computer you use the […]
Tech Term: Bandwidth

Here’s a question we want you to take a second to consider…How much do you rely on the Internet? The answer for almost everyone is that it is essential to your current quality of life. Technologies have been developed, industries have been launched, and literally billions of people use it every day, making it one […]
How to Properly Assess Your Technology Needs

Nothing lasts forever, especially not the technology that a business relies on to function. Between typical wear and tear and the always-improving trajectory that the technology industry follows, you will likely need to actively evaluate your needs and what you resultantly need to obtain. Today, we’ll walk you through how this technology assessment should be […]
Which Authentication Option is Best?

Smartphones have steadily increased in their capabilities, and as they have done so, they have resultantly gathered more and more data that needs to be secured against potential security threats. Fortunately, there are also more ways to protect your smartphone than ever before. For today’s blog, we’ll take a look of the options you have […]
Tip of the Week: Keeping Track of Your Inventory

Regardless of your organization’s size, there is more than likely a large amount of information technology to keep track of and maintain. As is usually the case when so many moving parts and variables are involved, the task of keeping them organized can quickly become difficult and stressful. This week, we’ll give you a few […]
Four Questions to Have About Cloud Services

Can you think of a more revolutionary technology in today’s modern age than cloud computing? Companies are now able to implement solutions that are both flexible and scalable enough to suit the needs of both small and large organizations. To this end, the same cloud won’t work for every type of organization. Here are four […]
Your Office Deserves a Good Cleaning

In keeping with the freshly rejuvenated feel that springtime brings, many people take advantage of this energy by doing some much-needed spring cleaning after the long winter months. Why shouldn’t the workplace join in the fun? In this blog, we’ll explain how a fresh and clean office can benefit your employees and your business as […]
Tech Term: Cookies Defined

Chances are, if you’ve spent any amount of time around a computer, you’ve heard of browser cookies. What you may not have heard, is what these cookies do. For today’s Tech Term, we’ll explore what cookies are, and what they do. What are Cookies? A cookie is a sample of information that a website stores […]
