Pop culture gives us an impression of what cyber investigations look like. Official-looking people, in impeccable suits, typing away at terminals and analyzing the data scrolling past them on their heads-up displays. In reality, computer forensics (as they are actually called) are a little less dramatic, and much more serious. For today’s tech term, we’ll dig into the field of computer forensics.
What are Computer Forensics, and What Are They Used For?
Computer forensics can be defined as the application of certain specialized techniques to locate and analyze the information on a computer or computer system, protecting it for use as evidence in a trial. Once the requisite warrants have been acquired, a forensic technician is tasked with isolating the device from outside influence by disconnecting it from the Internet before copying every file and poring over their contents for evidence.
The investigator must make a copy of these files so as to preserve the original evidence. Accessing a file can be enough to change it slightly, potentially rendering their evidence inadmissible.
Computer forensics can be leveraged in a wide variety of cases, as any given device may contain evidence of a crime to be, or that was, perpetrated, as well as effectively be the scene of the crime itself. An investigation dives deep, not only focusing on the presence of files, emails, or other documents pertinent to the case on the device, but also on an analysis of these items’ metadata, as it reveals when data appeared on a computer, when it was edited and saved last, and who the user was that carried out these actions.
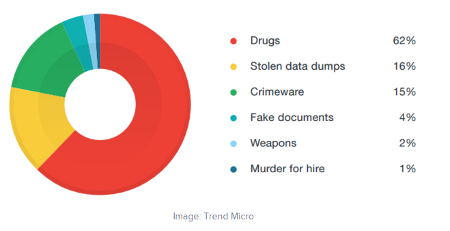
These methods have been used to crack cases involving a dirty laundry list of crimes, as this sample of their uses suggests:
- Intellectual Property Theft and Industrial Espionage
- Employment Disputes
- Bankruptcy Investigations
- Inappropriate Email and Internet Usage in the Workplace
- Regulatory Compliance
- Forgeries and Fraud Investigations
Alternative Sources of Analysts
Of course, law enforcement are not the only bodies that maintain and utilize computer forensics labs. Six major companies, including Walmart, American Express, and Target, have accredited laboratories, and there are countless other independent labs that have not been accredited. These in-house labs can often outperform traditional law enforcement groups, as they are better able to keep their solutions on the cutting edge.
In fact, these labs are often recruited by law enforcement to assist in solving crimes. Target’s labs have announced in the past that they have assisted with “felony, homicide, and special-circumstances cases” on a volunteer basis for years, a spokesperson claiming in 2008 that a full quarter of cases worked by Target’s laboratory had nothing to do with the company.
How Does Your Technology Compare?
If you want a team on your side that will take as much care to protect your solutions as a computer forensics team does to track down cybercrime, give NuTech Services a call at 810.230.9455.